There are certain factors in an email that have nothing to do with how well your email is written or designed, but still impact the effectiveness of your email marketing.
These factors are technical, and can be neatly summed up with the term “email authentication.”
Next to the quality of your email list, email authentication has the largest impact on your deliverability. And poor deliverability rates translate to poor ROI from your email marketing. A bounced email is no better than a deleted email. Maybe even worse, since your subject line and email content have no opportunity to work if the email is rejected or goes to the spam folder.
So, properly setting up your email authentication is the groundwork for maximizing your email marketing performance.
There are several parts to setting up a complete email authentication system. So, we’ve split this guide into a few pieces that you can read through as you need them.
We’ll start from the very basics.
What is Email Authentication?
Email authentication a set of methods that receiving email servers use to ensure that emails are not forged. Authenticating an email verifies that the email message actually came from the sender listed in the “from” field in the email header, and that the email wasn’t changed by someone while it was in transit.
Email providers use email authentication to protect users from spam, phishing scams, and other malicious emails.
Most authentication information is transmitted in the email message header. The person reading the email usually doesn’t see the authentication information. So, authenticating your emails has no impact on the quality of your email content.
Simple Mail Transfer Protocol (SMTP), the basic email sending protocol, doesn’t include any authentication mechanisms.
So, SPF, DKIM, and DMARC standards were developed to enhance the security of SMTP. We’ll cover these standards in detail a little further on. For now, just know that you need to use all three of them to get a fully functioning email authentication system.
How Does Email Authentication Work?
Although each of the three authentication protocols has a specific purpose and it’s own setup process, email authentication generally works like this:
- An organization or domain owner establishes rules for authenticating emails sent from all of its sending domains.
- The organization configures its sending email servers and email infrastructure to implement these rules.
- The email authentication rules are published in the DNS records (Domain Name System records) for each sending domain.
- Receiving mail servers authenticate emails from an email sender according to the authentication rules the sending domain has published.
- Receiving email servers handle emails according to the authentication results to correctly deliver, quarantine, or reject emails.
In order for email authentication to work, the sending and receiving email servers need to communicate and cooperate.
That’s why the three email authentication standards (SPF, DKIM, DMARC) were developed. This way, all email clients can be configured to use the same authentication standards. Otherwise, Gmail, Microsoft, Yahoo!, and every other email provider could use their own proprietary authentication methods, and email delivery would be a disaster.
Standardized email authentication provides certainty that emails are safe, and enables supervising organizations to track email sending behavior and assign sending IP address and domain reputations for weeding out malicious email senders.
Configuring your email authentication is fairly easy, if you know what to do. Even so, it’s best if you work with your development team or domain administrator to ensure that you get everything set up correctly.
Here’s what you’ll need to do to get your email authentication going.
Setup SPF Authentication
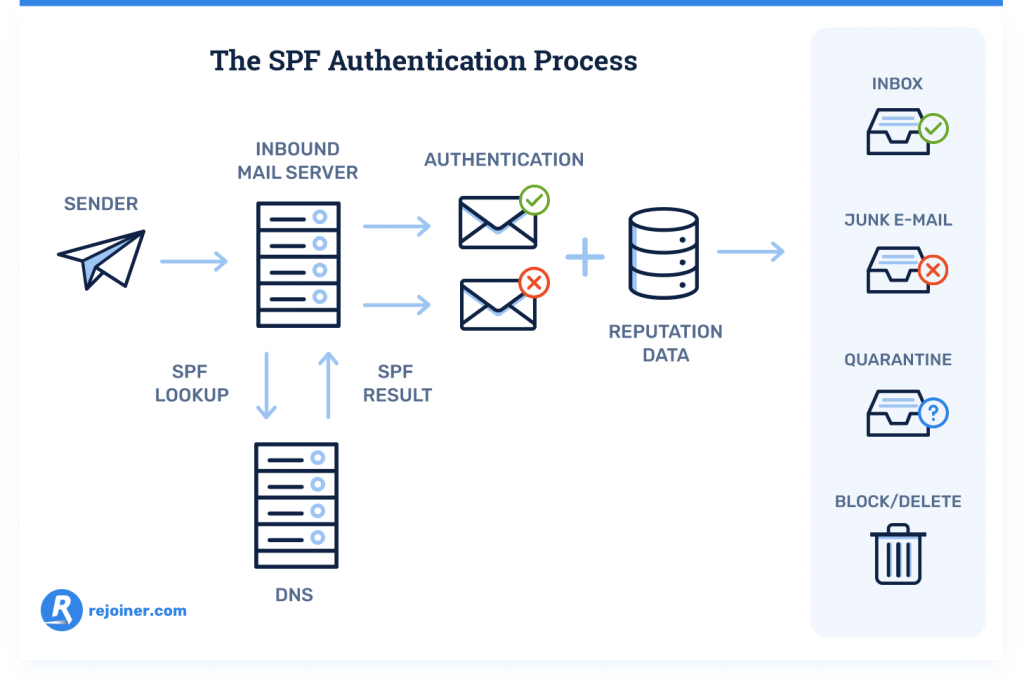
Sender Policy Framework (SPF) is the authentication standard that verifies your identity as an email sender. Without SPF authentication, your emails may get rejected because they look like they’re from an unverified sender address.
You’ll need access to your DNS records and a text editor for creating TXT records to configure SPF record.
Here’s a detailed guide on how to setup SPF authentication.
Setup DKIM Authentication

DomainKeys Identified Mail (DKIM) provides a unique public key that pairs with a private key to verify that an email is not forged or altered. Without a DKIM signature, your emails are susceptible to man-in-the-middle attacks where a bad actor changes your email while it’s en route to the recipient.
You’ll need a DKIM key generator, in addition to a text editor and access to your DNS records to setup DKIM authentication.
Here’s a detailed guide on how to setup DKIM authentication.
Establish DMARC Policies

Domain Message Authentication Reporting and Conformance (DMARC) creates policies for handling email messages that fail SPF or DKIM authentication, and messages that are missing one or both of those authentication standards. DMARC gives you more control over your email authentication system and makes your SPF and DKIM standards more effective.
You’ll need access to your DNS records and a text editor for creating your DMARC TXT record to configure your DMARC records.
Here’s a detailed guide on how to setup DMARC records.
Monitor the Health of Your Email Program
You can check your email authentication protocols any time you want. However, once your email authentication system is setup properly, email authentication should be nearly hands-free.
However, there are a few email marketing metrics that you can track to ensure that nothing has gone wrong with your email authentication. Spikes in your bounce rates, low deliverability rates, and other metrics indicate that you may need to revisit your email authentication setup.
Here’s a detailed guide on how to monitor your email campaigns.
If you get all three of these authentication standards setup, you’ll get the best deliverability rates. And, therefore, you’ll get the best ROI from your email marketing.
If you have a quality email service provider, they’ll usually ensure that your email authentication is up to par. Here at Rejoiner, we check the health of every client’s email program, and work with them to implement best practices and ensure that their emails are reaching the inbox.
But, no matter who takes care of your email authentication setup, there’s no way to get the most from your email marketing without it. When all your emails are being properly authenticated, you’ll see a boost in deliverability rates and email profitability.
What to Do Now
Did this post help you with your email authentication issues? Subscribe for more articles just like this.
Learn About Email Deliverability.
Want your email service provider to work with you to setup your email authentication? Schedule a free strategy session.






